

Architects are no strangers to controversy, but few have had their work called a “tip off [to] terrorists,” as The New York Times once described Deborah Natsios and John Young’s twenty year old project, Cryptome. Then again, few architects devote their time to disclosing government secrets, from the internal emails of Wikileaks to lists of alleged former members of the Stasi.
Cryptome is a repository of some 44.3 gigabytes of documents on dual-use technologies, military facilities, freedom of expression, cryptography, and other issues relevant to contemporary and clandestine governance. Its stark, Courier interface offers little assistance for the intrepid, post-social media era user. Yet its bowels contain provocative details on the infrastructure that enables contemporary surveillance, among many other things. As a whole, Cryptome amounts to perhaps the largest archive of entirely-uncensored information around. (Wikileaks, in contrast, censors the leaks it releases).their work reveals and exposes the often invisible, yet deeply material, operations underpinning contemporary urbanity
How does this relate to architecture? For one, Natsios and Young are practicing architects based in New York City, who find few points of distinction between their work with Cryptome and their design practice, Natsios-Young Architects, which is deeply committed to the social values of architecture. And while Cryptome may be unadorned, Cartome, which is something of a sister archive, includes provocative videos, maps, and other designed material. But most importantly, their work reveals and exposes the often invisible, yet deeply material, operations underpinning contemporary urbanity.
Over the course of several weeks, I exchanged emails with Natsios and Young (Natsios is the primary author of the responses, and any use of first person is from her perspective). In this two-part interview, we discuss their background, their motivations, and their understanding of privacy in the twenty-first century city.

Let's start at the beginning. You both had peripatetic childhoods. How have those experiences influenced your life and work?
The French colonial villa in Saigon that was one of my childhood homes is described in a recent book lit up by nighttime tracer shells, surrounded by gunfire and sprayed with bullets as South Vietnamese paratroopers and tanks mobilized along the street. We had moved on to Paris a few months before this incident, which turned out to be a failed military coup d'état against the presidential palace next door, and as the author notes, a successor family now occupied the place.
Well-defined logistics of residential succession shuttled us in and out of such homes in capital cities across Europe, Asia and South America that I lived in during the Cold War. These were local residences reserved for the covert CIA chief of station and his family during postings that customarily lasted from two to four years. In Paris, we abruptly relocated to a new address halfway through our tenure when, during the final throes of the Algerian war, the French owners of the property were forced back to the metropole from France's former North African colony. The houses were in some sense extensions of the capsule of embodied personhood that surrounds the diasporic individualYves Saint Laurent, himself born in Algeria, had just opened his first couture house in the townhouse next door as bombs were going off in the environs of the city and political graffiti was lacing urban walls.
These official houses exuded a distinctive poetics of space, each offering intensely felt architectures of sanctuary within politicized landscapes traveled by a border-crossing child. The houses were in some sense extensions of the capsule of embodied personhood that surrounds the diasporic individual––a portable enclosure of privacy, autonomy and imagination.
At the same time, this architecture of refuge was always understood as a contingent moment of local stasis within continual mobilizations across a residential network stretching into remote scales of geopolitical space. The clandestine housing matrix was one of the lesser known apparatuses of US Cold War national security infrastructure. It was not your postwar American suburb. But its logistical support for centralized intelligence collection, which was key to US postwar modernity, played a part in enabling the suburb's rise.

John's boyhood itineraries also evaded the presumably stabilizing frameworks of the emerging suburban consensus. His transiency through three dozen or so towns across Texas where his father sought manual work mapped itinerant labor at a more regional scale, though on one occasion, the world beyond became visible through a local frame. When he was quite young, his father took an odd job trucking prefabricated barracks formerly used to house German prisoners-of-war from one decommissioned Texas POW camp to another. Prisoners had since been repatriated to Germany. The barracks were not so different typologically from the spartan migrant worker dormitories father and son camped in when hired out as temporary agricultural labor. Prisons and worker dormitories disciplined docile bodies in similar ways.
On the prison camp job, John was handed a long pole with a hook at one end and tasked with lifting electrical wires running across the Texas roads high enough to allow his father's cargo safe passage beneath. His small act of childhood participation engaged the bundled architectures, infrastructures and logistics of national security networks––from transportation and utilities to carceral housing and the laws of war. Militarized infrastructures came into greater focus when he found himself a decade later in Cold War Germany serving the US Army of Occupation as a teenage soldier in the Corps of Engineers––housed, ironically enough, in former barracks of the German Army.While infrastructures may be described as blackboxed or culturally invisible, we always try to render their inherent politics and interests culturally visible.
Our unusual youthful mobility, both regional and geopolitical, anticipated by quite a few decades the circuits of geographical flow produced by restructured economies of today's globalizing world. Technologies for command-and-control, tagging, tracking, surveilling, listening, storing and databasing are built into the coordination and management of contemporary mobilities, whether commercial or military, benign or pernicious. These technologies have origins in security processes of the Cold War moment when signals intelligence (SIGINT) and human intelligence (HUMINT) filled in the blanks for incomplete doctrines of geopolitical containment. Building information modeling softwares (BIM) that have become our industry standard can also be traced to this legacy.
As licensed architects with an interest in decentralized zones where architecture and public infrastructures intersect, John and I distinguish ourselves from systems engineers who claim to be practitioners of a value-neutral technics. While infrastructures may be described as blackboxed or culturally invisible, we always try to render their inherent politics and interests culturally visible. Our work in support of a democratic society has always tried to equitably expand public goods in the public domain, public sphere and public space. In the information age, this includes Cryptome advocating for information equality and making visible to the public domain the knowledge-based economy's most blackboxed informational infrastructure: the corrosive apparatus of national security secrecy.

What guides your work as architects? Can you give me an example of a project that best exemplifies your approach to architecture?
We confess at the outset to never having worked on Mac OS platforms. John and I endorsed CAD tools earlier than most New York City architects, but came on board via PC platforms preferred by our engineering consultants. That we never joined the design world's clannish Mac tribe is a pretty good clue to our grounding––and undergrounding––in practices that tend to the culturally invisible: unpacking infrastructures, tinkering with their programming, patching their codes and their sustainable cultures of maintenance and repair. This is an open-ended process of everyday research. Cryptome digs in to shore up public domain infrastructures.Fee structures demand that service professionals be servile professionals
John and I had pretty strong graduate training in architectural theory and design at Columbia and Princeton, respectively, after pursuing underground majors in philosophy and mathematics, respectively. We later occasionally taught graduate architecture and urban design studio. But lived experiences in an increasingly privatized metropolitan milieu dominated by deregulated finance, insurance and real estate interests (FIRE) revealed the inherent vulnerability of architectural design negotiated from a seated position at the desktop. Fee structures demand that service professionals be servile professionals. Sedentary desktops and drafting chairs invite the abdication of the knowledge economy architect from messy dilemmas and material urgencies of the urban field lying beneath the glossy surface of screen simulations. Trending graphical interfaces distract with endless iterations of screensaver architectures destined to forever remain just one pixel deep.
We support the street as the reigning public infrastructure of the city's complex social and material world of mobile, everyday living.Unmoored childhoods may account for why, as intensive pedestrians, John and I maintain strongly visceral attachments to the lived urban street. We support the street as the reigning public infrastructure of the city's complex social and material world of mobile, everyday living. It's no surprise we take seriously the architect's obligations to secure visceral public goods identified in professional codes as public health, public safety and public welfare (HSW).
Infrastructural goods for evolving HSW frameworks constitute the architect's terrain of fundamental service in the democratic public sphere, on the street and beyond. In an information society, robust democratic access to information is crucial for HSW integrity. Over the years, we've been doing ongoing public domain work of this kind at an 18,000 square foot urban lot zoned M1-4 for industrial and manufacturing uses. Trusses of one of city's massive steel bridges cantilever nearby. The lot's three built structures, one dating from 1919, house the studio complex of a noted artist of large-scale sculptures that have been publicly sited in cities worldwide. At the same time, the artist's 'public' works are valuable currency in highly privatized circuits of the $64 billion global art market driven by a frenzied collusion of elite galleries, museums, culture media, auction houses and private collectors.
How are these public and privatizing values reconciled? We propose alternative strategies for service in the public interest when approaching the material frameworks where the artist's high-value works are modeled. Gritty fieldwork and forensics are key to assessing the lifecycles of older urban structures. Fractured masonry facades, leaks and depressed sidewalks document the effects of stress under the ravages of the neighborhood's heavy industrial traffic. Threat of structural collapse into the street augurs performance art with a stark public finale. Galleries and museums cannot mediate vital material conditions that directly impact the life outcomes of urban populations.Anonymous interventions straddle the boundary of cultural invisibility and visibility.
Our various low-key interventions have introduced shoring details for structural stabilization, sidewalk remediation for elimination of hazards, targeted moisture protection to batten down failing building envelopes and HSW code-compliance as an ethical practice. Galvanized steel cables, lag bolts, 2X10 members, concrete and epoxy reinforce the neighborhood's extant fabric at an embodied scale of the local. Interventions are crafted with an artisanal awareness of legacy material culture, engineering, urban history and, whenever possible, engage tactical skirmishes against encroaching FIRE interests.
Anonymous interventions straddle the boundary of cultural invisibility and visibility. They acknowledged crucial background traditions of maintenance and repair being devalued by privatized cultural processing that is increasingly fixated on marketing elite brands and global reputations. We are satisfied that our details have completely vanished into the fabric that knits the democratic city together in equitable, everyday ways.
How did you first get introduced to the world, so to speak, of encryption, secrecy, and information?
We discovered after entering the pre-browser world of online gophers and listservs in the early 1990s that architectural CAD users seemed largely disjoint from radical changes afoot in the emerging information economy. Computing capabilities were welcomed as a boon to the production of architectural drawings and specs, as were profit-making advantages of labor power provided by indentured CAD jockeys saddled to new production tools. But social transformations and politics inherent in powerful information and communications softwares, hardwares and networks didn't show up on the architect's radar. Architects were not engaged even if compelling issues of public domain, public space, information equality and privacy had powerful spatial implications for an urban context being challenged by trending privatization. The ascendancy of the 'smart' city has underscored these issues decades later.power in the knowledge society is vested in such programmers of vital networks
Radical coders, cryptographers and technologists of the online Cypherpunks mailing list were foregrounding such politics in vigorous terms when we ran into them during those early years. Manuel Castells has pointed out that power in the knowledge society is vested in such programmers of vital networks. Our youthful experiences of Cold War national security and intelligence infrastructures resonated with C-punk debates about the impacts of government surveillance, the control of information and the need for strong encryption to protect individuals from unacceptable violations of privacy.
John became active in C-punk debates at about the time we pretty much ruptured from our cohort of traditional analog architects. The latter continued to perform the service role of nostalgic stylists even as an accelerating world was appropriating the title 'architect' for technologists who were structuring vital informational and communications systems.

How would you describe the ethos of Cryptome? What motivates you to disclose information?
Whenever we describe Cryptome as a library for information equality dedicated to banned documents, we take stock of a couple of brick-and-mortar library projects we've been involved in over the years on academic campuses around New York City. Architectural services ranged from providing new programmatic spaces, HVAC systems and elevators, to fireproofing stacks, installing innovative compact book storage systems and retrofitting accommodations for new technologies. Over the years, as compact book systems yielded to digital storage, we watched the title of Chief Librarian shift to Director of Information Technologies.
free access to knowledge is fundamental to democratic self-ruleCryptome is pleased to test the boundaries of the claim Thomas Jefferson made when the private library he assembled at Monticello––the home he designed for himself––was acquired as the basis for the new Library of Congress. Jefferson argued that free access to knowledge is fundamental to democratic self-rule. He believed it critical to transforming the subjects of kings into citizens of a republic, as Abby Smith Rumsey has described. Jefferson's coordinated activism as brick-and-mortar designer and information architect is a legacy that can even begin to redeem his tarnished role as unreconstructed slave owner.
Current trends to privatize information, whether in private sector or by the state, run counter to such foundational democratic sentiments. The corrosive effects of the bloated empire of national security secrecy on any robust democracy has been well documented. We recommend the Washington Post's thorough investigative series of 2010 titled 'Top Secret America'.
Current trends to privatize information... run counter to such foundational democratic sentimentsToo few architects are aware of the American Library Association's commendable role supporting information activism in the digital era. Far from becoming obsolete, the brick-and-mortar public library has become a site of embodied work on behalf of information equality. Consider the vividly architectural imagery of the ALA's 2014 statement applauding a Fourth Amendment ruling by the Supreme Court on the constitutionality of cell phone searches:
“In the past few years, our cell phones have become mobile libraries capable of storing massive amounts of personal and private data about our lives. The Constitution does not give law enforcement the right to conduct unlawful searches of our cell phones—many of which contain immensely personal information, such as our private conversations, photos, videos, banking information and website history. In the same manner that we would not allow police officers to search unlawfully through our home library bookshelves without a warrant, we cannot allow government officials to search freely through our cell phones.”
What distinguishes Cryptome from other public domains of information, such as Wikileaks perhaps? Do you consider your work akin to journalism?
Activists in the broader information ecosystem are not protected by traditional press freedoms but are nonetheless shifting the traditional definition of journalism and journalistic practice. Julian Assange calls himself a journalist to benefit from the umbrella of press protections. Cryptome was denied press credentials by the NYPD office that issues them.
Activists in the broader information ecosystem are not protected by traditional press freedomsCryptome believes the resiliency of the informational commonweal is best supported by multiple redundant sites inflecting the ecosystem in low profile rather than projecting as grandiose monuments.
Julian Assange was a rather quiet Cypherpunk during the formative period described above. He went on to embrace a more voluble, self-promotional brand identity after founding Wikileaks. His public relations-enhanced trajectory went on to have dire consequences for him personally, and perhaps for Wikileaks as well. This cautionary parable applies equally to the architecture profession's surrender to starchitecture's merchandising economy.

Can you talk about the design of the site? I think some people used to Web 2.0, if you will, might be overwhelmed by the mix of Courier and the paucity of visual hierarchies.
We're very receptive to your diagnosis of the site's overwhelmingly non-hierarchical visual codes!
Being known for an unpolished DIY presence may be a tad perverse in this age of designer flash bells, whistles, eye-candy and banner ads. We hope self-guided learners remain active, engaged and criticalThis un-adorning reflects our concern with design skill being hijacked by market-driven branding and merchandising campaigns.
At the same time, we're pleased to provide an unadorned boot camp for reader autonomy, choice and self-guided learning that we believe crucial to self-determination. Readers use search engines for self-guided research. We hope self-guided learners remain active, engaged and critical. This would distinguish them from consumers who are rendered passive while whetting online desire.
I'm also interested, more generally, in how design figures into your work as Cryptome and Cartome. When does design become a tool rather than an anaesthetic?
You raise a productive distinction between the two economies of information: Cryptome's 'banishing' of design as a counter-market strategy contrasted with the more intensely articulated cartographic narratives inventoried at Cartome, a research zone embedded in the larger site.
One the one hand, Cryptome presents its scrolling index as a culturally invisible, somewhat anonymous feed. We've described our recent 50-minute animated scroll of the full 1996-2016 index as something of a deterritorialized, non-wayfinding map. In most cases, the informant or witness also happens to be an autobiographical subjectThis unadorned fugitivity or abnegation charts evasive lines of flight in the face of mobile authorities that are continually tracking our site. We've stated elsewhere that the scroll “recapitulates the flowing time and space of two decades of Cryptome's information politics as a kind of borderless textual liquefaction that is hard to pin down.”
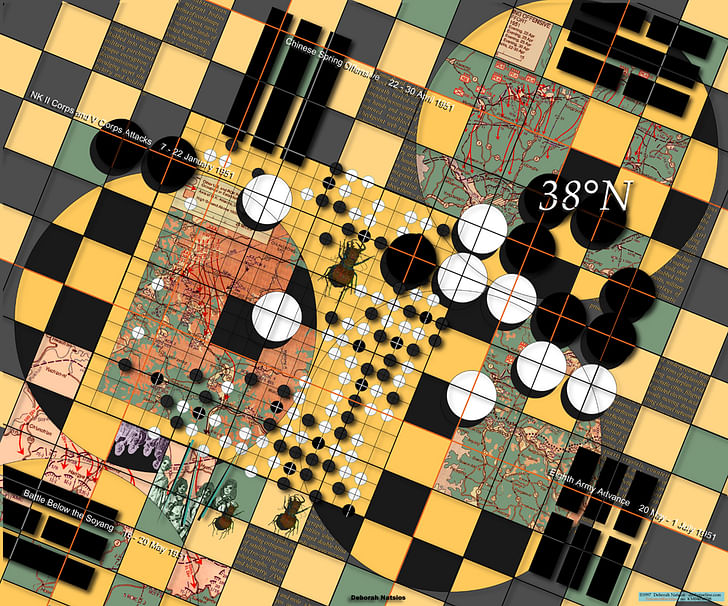
At the same time, our cartographic pieces are constructed from very articulated visual codes. This granularity and color coding supports demotic micro-history recounted 'from below'. Narrative codes attempt to reverse the silencing of micro-historical accounts otherwise suppressed by dominant geopolitical historiographies. Cartographic assemblages like L'Empire des Oiseaux, Irredenta in the Eurozone and Parallel Atlas 39°N take on something of artisanally crafted texture while enabling the voice of unheard informants. In most cases, the informant or witness also happens to be an autobiographical subject. Maybe these projects can be thought of as musical notation in that they encode and map the orality and aurality of previously unheard voices within geographic space.

I've read that you've had more than your fair share of visits by the FBI. Yet, while Chelsea Manning and Barrett Brown are behind bars, Julian Assange is trapped in the Ecuadorian Embassy, and others, such as Aaron Schwartz, are dead – well, here you are. Alive and not in prison. What's the legal status of your work? How do you avoid prosecution?
We acknowledge that programmers of dominant networks hold great power in our knowledge economy. Radical programmers are targeted by powerful interests during ongoing processes of calculating and managing risk to the critical networks these programmers may be accessing, reverse-engineering, hacking or simply critiquing.
Let us assume our efforts on behalf of code-mandated criticalities of public health, safety and welfare are being tolerated.We've referred in the past to Edward Snowden as a cyborg with a conscience gone rogue inside a large technical system (LTS). As architects involved with LTS infrastructures who are not programmers, we've managed to find a way to both engage vital debates about networks as well as chart lines of flight that keep us in the clear.
Since 9/11, New York State has issued an ID card that grants us licensed professionals special access to sites during times of emergency and critical need. Let us assume our efforts on behalf of code-mandated criticalities of public health, safety and welfare are being tolerated. We'll leave it at that.
Check back soon for part two of our interview with Cryptome.
This feature is part of Archinect's special thematic focus for June, Privacy. For more on the changing meaning of privacy in the digital age, check out other features.
Writer and fake architect, among other feints. Principal at Adjustments Agency. Co-founder of Encyclopedia Inc. Get in touch: nicholas@archinect.com
No Comments
Block this user
Are you sure you want to block this user and hide all related comments throughout the site?
Archinect
This is your first comment on Archinect. Your comment will be visible once approved.