

Cybersecurity: you hear about it often, but assume it doesn’t really concern you. You have nothing to hide, right? And, besides, why would someone hack you of all people? Or your firm?
The world of cybersecurity may seem the haunt of technologists and specialists, but you inhabit it as well, whether you buy weed on the dark web or not. Security and encryption technologies are woven into the fabric of the internet and, by extension, everyday life. That’s what the “s” in “https” signifies, which prefaces your access to Facebook, Amazon, Google Docs. And, as the recent face-off between Apple and the FBI exposed, your iPhone is a heavily-encrypted device, a veritable safe strong enough to hold back even the best of hackers—in some cases.Unless you’re cautious, you’re essentially an open book, readable by anyone literate enough.
But that doesn’t mean your data is secure. Unless you’re cautious, you’re essentially an open book, readable by anyone literate enough. Obviously this has tremendous repercussions for what privacy means today. As Edward Snowden’s NSA leaks revealed, the US government engages in massive data sweeps of American citizens, as well as foreign governments and their citizens. And hackers, likewise, can potentially do just about anything with your gadgets, from reading your emails to activating your iMac’s camera without your knowledge. As we incorporate digital technologies more and more into our life, particularly with the so-called “Internet of Things,” issues around digital privacy become spatial concerns as well.
Security is a journey, not a destination.There are many measures one can take to protect their virtual identity, from using Tor browsers to encrypted email services. But for the purposes this article, we’re going to take a look at a few common vulnerabilities an architecture firm may face, and what can be done to prevent intrusion. According to Paul Ducklin, senior technologist at cybersecurity service Sophos, “You need to make security part of your digital lifestyle. Security is a journey, not a destination.”
First, let’s start with some common attacks:

Phishing
You’ve probably received a warning email or two about phishing attempts in the past. Phishing is one type of social engineering, which, like those emails you get from people pretending to be heir-less royals, is a form of psychological manipulation with the intent to get valuable information from you.
learn to closely examine suspicious emails asking for sensitive informationPhishing, specifically, refers to attempts to get sensitive information such as passwords or credit card numbers by impersonating a trustworthy entity. For example, you may get an email from what looks like Google asking you to confirm your account information. At a glance, the email formatting will look like Google branding, although you can usually notice small discrepancies from looking closely.
To avoid falling for a phishing attempt, learn to closely examine suspicious emails asking for sensitive information. Poorly-translated language is often a sign that the email isn’t authentic. Don’t ever go to your bank’s website by clicking on an email link—the same goes for Paypal, Facebook, etc. Finally, make sure you only ever enter sensitive information on secure sites, ie. one’s the have an “-s” after “http”.
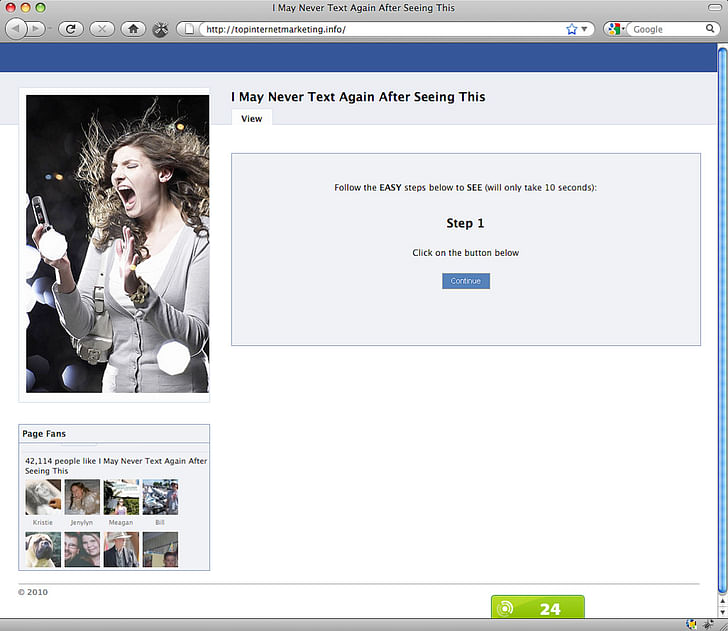
Clickjacking
Clickjacking, also known as a user interface redress attack, refers to attempts to trick a user into clicking a link that you didn’t mean to click on. For example, a website may have a button that looks nearly identical to the button you should click on, but instead it takes you to a website other than the one you intended to go to, or starts a download you didn’t want. If you stream shows online, you’re probably familiar with clickjacking attempts.If you fall for a clickjacking attack, your private information can be stolen or your computer can even be taken over
If you fall for a clickjacking attack, your private information can be stolen or your computer can even be taken over. Depending on your browser, there are extensions that can warn you if there’s a clickjacking attempt on a website you’re visiting. For example, here’s one for Google Chrome.
Drive-by download
A drive-by download can be the result of something like clickjacking or can occur when a user knowingly downloads a file, but doesn’t understand what it is. For example, someone at your firm may try to download a torrent of a vector library. In that file is an executable that includes a virus, that then wipes out your system.

Ransomware
Ransomware, which is pretty much what it sounds like, is one of the biggest threats a company may face. In short, a hacker gains access to a network—typically through something like a phishing attempt or clickjacking—and encrypts the data. They will then hold it ransom until the company pays up, usually through a cryptocurrency like bitcoin.
Once you’ve paid the ransom, you have to wait for a decryption key. If it comes (and this isn’t guaranteed), cross your fingers all your data is still there. In the meantime, you’ve lost hours of work and labor, as well as the ransom money.
In the past few years, the number of ransomware attacks have skyrocketed as access to cryptocurrencies has become easier and more mainstream.
What to do:
There are many other types of malwares and viruses and possible modes of attack out there. But one thing you may have noticed is that these all involve human error rather than some slick sunglasses-wearing fellow in a trenchcoat plugging into a dataport on the side of a building.
“For us, the most vulnerable is anywhere you have a human being deciding what questions to answer and what things to click on,” John Robison, the COO of architecture firm KTGY told me over the phone.the best business continuity plan... would be to be able to rebound from an attack.
“Teaching people what the threats are, what to be conscious of, how to spot the dangers, things that are red flags,” states Robison. “End user training is probably the most effective when it comes to things like malware, ransomware.”
Most large firms like KTGY will have all the best desktop software and backend protection, but “the crooks are usually well ahead of that, so they catch the old known ones but they don't catch the zero-day ones,” Robison tells me.
But what do you do when a ransomware attack succeeds?
According to Robison: “the best business continuity plan for us would be to be able to rebound from an attack.” That means consistently backing up your data, so that if it’s taken hostage, rather than spending hours and money trying to work with the criminals, you can reboot your system anew.
This sentiment was echoed by Ducklin: “One of the biggest cybersecurity risks to businesses, especially small-to-medium companies, is ‘putting off until tomorrow what you can do today.’”
One of the biggest cybersecurity risks to businesses... is ‘putting off until tomorrow what you can do today.’“Missed backups, for example, make the potential cost of ransomware much higher,” Ducklin explained. “Missed patches make the risk of malware infection higher in the first place.”
Robison verifies this assertion, noting that, when it comes to a ransomware attack, it’s a game of cost-benefit analysis in terms of lost hours of work. “Say you lost three and a half hours of work, that's probably better than sitting around for how long looking for the ransom to be paid and hopefully get the decryption key.”
Ultimately, it doesn't matter if you're trading state secrets or stair sections, cybersecurity affects us all.
This feature is part of June's special thematic focus, Privacy. Do you have projects that grapple with changing notions of privacy today? Submit to our open call by Sunday, June 19th.
For more tips to on how to #getsafe, check out the Sophos site.
Writer and fake architect, among other feints. Principal at Adjustments Agency. Co-founder of Encyclopedia Inc. Get in touch: nicholas@archinect.com
No Comments
Block this user
Are you sure you want to block this user and hide all related comments throughout the site?
Archinect
This is your first comment on Archinect. Your comment will be visible once approved.